Posts

King’s Speech Highlights Security Laws
Following the State Opening of Parliament, the King’s Speech on 17 July included news of significant new legislative proposals to address cyber security concerns, focusing on supply chain risks, particularly in the public sector, and improving…

UK Company Scammed $25 Million Via Deepfakes
It’s been reported that an employee at London-based design and engineering multinational, Arup, was duped by a deepfake video call into paying a staggering $25.6 million to fraudsters.
What Happened?
According to reports…

Wales Has Put A SOC In It
The UK’s first national security operations centre (SOC) known as CymruSOC, has launched in Wales to protect the country’s local authorities and fire and rescue services from cyber-attacks.
SOC
The Welsh government…

‘Networkless’ Attacks?
In this article, we look at why and how networkless attacks (which target cloud apps and identities) have created new opportunities for attackers and new risks for businesses, plus what your business can do to mitigate these risks.
The…
New Quantum Attack-Proof PCs
At its Annual Partner Conference 2024, HP announced the world’s first business PCs to protect firmware against quantum computer attacks.
This Issue
As highlighted by Global Risk Institute research, 27 per cent of experts…

What Does Incognito Mode Actually Do?
Following news that Google may need to pay $5 billion over tracking millions of people who thought they were browsing privately through incognito mode, we look at what incognito mode actually does.
Incognito Mode
Different browsers…

New Privacy Features For Facebook and Instagram
Meta has announced the start of a roll-out of default end-to-end encryption for all personal chats and calls via Messenger and Facebook, with a view to making them more private and secure.
Extra Layer Of Security and Privacy
Meta…

Cyber Attacks Burn Out Security Experts
A new survey from CyberArk has revealed that increased workloads caused by a surge in cyber threats and attacks has led to 59 per cent of UK senior cyber security professionals facing burnout.
Cyber Crime Levels High
The results…

Microsoft Launches New AI Content Safety Service
Microsoft has announced the launch of Azure AI Content Safety, a new content moderation service that uses AI to detect and filter out offensive, harmful, or inappropriate user and AI-generated text or image content.
What Kind of Harmful…

Safety Considerations Around ChatGPT Image Uploads
With one of ChatGPT’s latest features being the ability to upload images to help get answers to queries, here we look at why there have been security concerns about releasing the feature.
Update To ChatGPT
The new ‘Image input’…

Firefox Helps You Hide (Your Emails)
Following several months of testing, Firefox users can now take advantage of the Firefox Relay email masking tool from within the browser to help preserve their online anonymity and boost security.
What Is Firefox Relay?
Firefox…

New Chatbot Attack : “Unstoppable”
Researchers at Carnegie Mellon University have reported finding a simple way to exploit a weakness and disrupt major chatbots like ChatGPT, Bard, and others.
Incantation
The researchers discovered that if they add specifically…

Government Pushing For Right To Spy On WhatsApp Users (and others)
The recent amendment to the Online Safety Bill which means a compulsory report must be written for Ofcom by a “skilled person” before encrypted app companies are forced to scan messages has led to even more criticism of this rather…

Snooper’s Charter Updated. (Poorly)
Amendments to the UK Online Safety Bill mean a report must be written before powers can be used by the regulator to force tech firms to scan encrypted messages for child abuse images.
What Is The Online Safety Bill?
The Online…

What’s Involved In a ‘Pen-Test’ ?
If you’d like to know what a ‘Pen Test’ is and the sorts of things you can expect from one, this article will give you a helpful overview.
Pen Tests
Put simply, pen testing is short for “penetration testing” and in a virtual…

What Are ‘Zero-Day’ Attacks?
In this tech insight, we look at what ‘zero-day’ attacks are, then look at some recent high-profile examples and ultimately at what businesses can do to protect themselves from zero-day attacks.
Sophisticated Attacks That Highlight…

11% Of Female Gamers Left Suicidal By Online Abuse
New Sky Broadband research has revealed that the level of abuse suffered by female online gamers from male gamers has been so strong that over one-in-ten (11 per cent) have been left feeling suicidal.
Shocking Levels…

Two Key Cyber Security Insights
With phishing attacks being favoured for their effectiveness by attackers and most ransomware attacks now targeting backup storage, we look at what businesses can do to protect themselves.
Spear Phishing Accounted For Two-Thirds…

View Deleted WhatsApp Messages
In this Insight, we look at how it is possible to uncover and read deleted messages on WhatsApp, and what a number of privacy features on the app mean for business users.
Changes
WhatsApp have made changes as regards message…

Passwordless Future : Google ‘Passkeys’
Google has announced the rollout of ‘Passkeys,’ which it describes as “the easiest and most secure way to sign-in to apps and websites” and a major step toward a “passwordless future.”
Working Toward A Passwordless…


Quantum Threat Growing
Following large investments in quantum computing followed by the ensuing advancement of this technology in recent years, as well as looking forward to benefits this could bring, there is also the growing threat of ‘quantum hacking.’
Quantum…


How To Spot Fake Images
With deepfake images recently making the news by fooling many people, we look at the issues around fake images and how to spot them.
Recent Examples
The emergence of AI has led to an increasing output of highly convincing fake…


What’s All the Fuss About A National Alarm?
With the UK government’s new ‘Emergency Alerts’ system now live, we take a look at what it is and how it will work.
What Are ‘Emergency Alerts’?
The UK government’s Emergency Alerts service, managed by the…


World Backup Day Is An Important Reminder
World Backup Day founder, Ismail Jadun, has said that March 31 will “will make everyone think about their situation, learn about the various options and get their files backed up”.
World Backup Day
World Backup Day, first…


WhatsApp’s UK Threats Over Online Safety Bill
The boss of WhatsApp, Will Cathcart, has said he would rather stop users in the UK from using the app than lower its security, as suggested by the UK’s Online Safety Bill.
End-to-end Encrypted App
One of the key security features…


New Meta Verified Blue Badge Subscription Service
Meta has announced it’s launching its own version of Twitter’s Blue Tick called ‘Meta Verified’ for Facebook and Instagram where users pay a monthly subscription to be verified on the platforms.
Announcement
On February…


IT Security Threatened By Professional Burnouts
A Mimecast spokesman has warned that in a labour market already stretched by shortages, Dutch digital resilience could be threatened if more attention isn’t paid to the mental well-being of cyber security professionals.
Wanting To…


2FA Storm At Twitter
Twitter-owner Elon Musk’s latest decision to turn off SMS 2FA after 20 March unless you pay for Blue Tick has caused another storm of criticism.
What And Why?
On 15 February, Twitter announced that: “starting today, we…


What Are SPF, DKIM, And DMARC Records?
In this insight, we look at the popular email authentication protocols SPF, DKIM, and DMARC, how they work, why they’re important, and what happens if they’re not set up properly.
What Is SPF?
SPF, or Sender Policy Framework,…


Do Hackers Get Pensions & Sick Pay?
Kaspersky research has shown that hackers are now being recruited with dark web job ads offering huge salaries and benefits!
What?!
According to Kaspersky’s analysis of more than 200,000 employment ads posted on the dark…


What’s All the Fuss About LastPass?
Following news that hackers have stolen encrypted backups from the parent company of popular password manager LastPass, we look at what password managers are, plus the implications of the attack for businesses.
Password Challenges
We…


Fewer Victims Pay Ransomware, Yet More Victims
Blockchain data platform Chainanalysis has reported that cybercriminals have seen a 40 per cent fall in their earnings as more people have refused to pay the ransom following ransomware attacks.
More Strains With Shorter Lifespans
However,…


Smart Products Have Just 2 Years Of Life
Consumer champion Which? says that high-end smart products may lose features and functionality, or become a hacking risk, after as little as two years because manufacturers may stop tech updates.
Stopping The Smart Updates Limits Lifespan
Which?…


A Lack Of Cyber Professionals
(ISC)2’s 2022 Cybersecurity Workforce Study has highlighted how the workplace skills gap, particularly the gap in the number of cyber security professionals, has grown by 26.2 per cent in the last year.
All Time High – But Still…


Forget Hacking, What About Tracking?
In this article, we look at the many different ways we are being tracked online, plus which measures users can take to avoid being tracked.
Why Are We Being Tracked?
Internet tracking is used for a number of reasons, including:
Improving…


What Are ‘BEC Campaigns’?
In this insight, we look at what BEC campaigns are, their characteristics, together with what businesses can do to protect themselves from the threat of BEC campaigns.
What Is A BEC Campaign?
A business email compromise…


GMA Announces Commitment to Growing Cybersecurity Success by Becoming a Cybersecurity Awareness Month 2022 Champion
Gregory Micallef Associates Limited (GMA) announced this week that it has signed on as Champion for Cybersecurity Awareness Month 2022.
What Is Cyber Security Awareness Month?
Founded in 2004, Cybersecurity Awareness Month, held each…

The Anatomy of a Data Breach: And Four Steps To Protect Your Business
Arguably no phrase has dominated the tech world the last 24 months more than the term “data breach.” From breaches that have impacted critical infrastructure like the Colonial Pipeline to hackers compromising healthcare records at UC San…


Nearly Half of Employees Use Risky Login Practices
A new study by 1Password has revealed that almost half of employees put their companies at risk by using risky online habits to avoid difficulties logging in and out of apps at work.
Taking Risks With Company Security
The study,…


Sharing Files That Self-Destruct
In this insight, we take a look at some of the many options available for sharing files that self-destruct.
Why?
Many business IT users have occasions where they need to send sensitive information, e.g. passwords and other private work…





Tech Tip – Stay Organised In Chrome By Pinning Important Tabs To The Left
If you’re working with lots of tabs open but want to be able to quickly locate essential web pages in your Google Chrome browser, try pinning important tabs to the left-hand side. Here’s how:
Right-click on the tab and select ‘Pin’.The…


UK Broadband And Mobile Carriers Face Tough New Security Rules
The UK government’s Department for Digital, Culture, Media and Sport has proposed a new set of rules to tighten up network security against cyberattacks in broadband and mobile carriers.
Amongst The Strongest In The World
The…





Tech Tip – Get Creative And Save Or Share Sketched Ideas Using Google Canvas
If you’d like a really fast way to sketch out your creative ideas on a digital canvas and quickly download or share the image, try Google Canvas. Here’s how it works:
Go to https://canvas.apps.chrome/.Choose a pen, pencil, crayon, eraser,…


The True Cost Of Using Pirated Software
In this article, we look at how the risks to businesses posed by pirated software can far outweigh the benefits of using it, and how you can protect your business from the true costs of pirated software.
Benefits
On the surface,…





Tech Tip – Stay Organised With Microsoft To Do’s ‘My Day’
If you’d like to improve your productivity and focus on daily tasks, but in a way that works with your existing behaviour patterns, and doesn’t create ever-longer to-do lists, ‘My Day’ in Microsoft's ‘To Do’ cross-platform app may…


Protect Yourself From Job Phishing Scams
In this article, we look at what ‘job phishing’ is, how it works, and how you can protect yourself from this type of fraud.
What Is Job Phishing?
Job phishing refers to recruitment/employment scams where fraudsters pose as…





Tech Tip – How To Use Notepad To Test Your Antivirus
Here’s a simple tip using Notepad to check if your antivirus is working as it should:
Open Notepad.Type X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H* into notepad.Save the file as either e.g., test.exe or test.bat…


Major NHS Supplier Hit By Ransomware Attack
Advanced, an IT supplier to the NHS, has been hit by a ransomware attack that could take a month to recover from.
What Happened?
Birmingham-based ‘Advance’ provides digital services to the NHS such as patient check-in and…


Pros and Cons of Weakening Encryption
With the Online Safety Bill threatening to undermine end-to-end encryption, we look at the strengths and weaknesses of this security trade-off.
Encryption
Encryption comes from the science of cryptography. In today’s digital…


How To Fake Someone’s Voice
Following recent security concerns about Amazon’s plans to enable Alexa to mimic voices, we look at how easy it is to do, what the benefits are, and what risks it poses.
Alexa The Mimic
Recently, Amazon announced that it was…


New Windows Feature Displays Which Apps Have Been Listening-In
The new Privacy Auditing feature in Windows 11 allows users to see a list of which apps have accessed their microphone or camera recently, plus details of any other suspicious activity.
See Which Apps Have Accessed Your Microphone…


How Can You Protect Yourself From ‘Identity Theft’?
With identity theft and the resulting identity fraud becoming more widespread, we look at how to spot the signs that you may be a victim, the effects on victims, plus how to reduce the risk of having your identity stolen and used for fraud.
What…


Russia Cautions Cyber Attacks May Start Military Confrontation
The growing number of cyber-attacks since the start of Russia’s war against Ukraine have led The Russian Foreign Ministry to warn that more western cyber-attacks on its infrastructure could lead to a direct military confrontation.
Housing…


New Spy-Spotting App From MI5
The UK government’s MI5-run ‘Centre for the Protection of National Infrastructure’ has launched a new app to help people spot approaches from foreign spies and organised criminals seeking sensitive information.
Really? How Big…


Apple, Google and Microsoft In Password Collaboration
Apple, Google and Microsoft have announced that they are joining forces to support a common passwordless sign-in standard that will allow websites and apps to offer consistent, secure and easy sign-ins across devices and platforms.
The…


Pernicious Pegasus Plagues (Another) Prime-Minister
With many governments (including the UK Government) being targeted with Pegasus phone-spying software, there’s now news that Spain’s PM’s has also been hit.
What Is Pegasus?
Pegasus spyware is sold by Israeli-based NSO Group…


Pegasus Spyware Discovered In Downing Street
The University of Toronto’s Citizen Lab has reported finding evidence that Pegasus spyware was being used to listen-in on UK government networks for 10 Downing Street and the Foreign and Commonwealth Offices (FCO) in 2020 and 2021.
Pegasus
Pegasus…


Warning: Scam Aid To Ukraine Emails Circulating
The UK’s national fraud reporting centre, Action Fraud, says that it has received 196 reports of scam emails claiming to be raising funds for victims of the war in Ukraine.
Facebook Post
In a Meta / Facebook post on…


What is Lapsus$?
In this article, we look at the cyber-crime gang Lapsus$, how they operate and the details of some of their recent high-profile attacks.
Lapsus$ ?
Lapsus$ is reported to be a mostly teenage cyber-crime gang (hackers), mainly…

Germany Warns Against Use of Kaspersky Anti-Virus
Germany’s Federal Office for Information Security (BSI) has warned that Russia-based Kaspersky’s anti-virus software could be used for spying or launching cyber-attacks.
Russian Companies Forced To Launch Cyber-Attacks?
The…


Stop Your Smart Devices From Being Used To Spy On You
With so many smart devices now all around us in homes and offices, we look here at ways to minimise the risk of having your privacy invaded.
The Internet of Things (IoT)
IoT devices are those devices that are now…


3% of Users Responsible For 92% Of Breaches
A report by Security Company ‘Elevate’ has revealed that 3 per cent of users are responsible for 92 per cent of malware events for businesses, indicating that a small number of users create the most risk.
2016 to 2021
‘The…


Mobile Malware Surges By 500%
Proofpoint researchers have reported that, starting in early February, there has been a 500 per cent jump in mobile malware delivery attempts in Europe.
Trend
According to the researchers, this rise is in keeping with a trend…


How Worried Should We Be About Cyber Warfare?
In this article we look at how cyber-attacks have been used by Russia against Ukraine, how this may spread to other countries, and what businesses can do to prepare.
Cyber Attacks – A Part of ‘Hybrid Warfare’
State-sponsored…


Ransomware Study : Most UK Firms Pay
A study by security firm ‘Proofpoint’ has revealed that 82 per cent of UK organisations whose systems were infected by ransomware in 2021 opted to pay the ransom.
Much Higher Than The Global Average
Despite cybersecurity and…


Firms Prepare For The Quantum Apocalypse
In this article, we look at what the ‘quantum apocalypse’ is, and what businesses are doing to prepare for this threat.
What Is The Quantum Apocalypse?
The so-called ‘quantum apocalypse’ refers to the unspecified point…


Why Solid Black Bars May Be Best For Redacted Text
In this insight, we look at how to best to avoid redacted text from being ‘unredacted’ by certain software tools, and we look at what researchers advise based on recent experiments.
The Problem
For businesses and organisations,…


Ex School IT Technician Jailed For Cyber Attack
A sacked school IT Technician who took revenge by deleting data and sabotaging his old school’s network (and by wiping the computers of everyone who was logged in) has been jailed.
Revenge Hack
As reported on Leicestershire…


What Is The Online Safety Bill?
Following recent announcements of a toughening-up of the (draft) Online Safety Bill, we look at what the bill is, and what its implications are.
What Is The Online Safety Bill For?
The UK government’s Online Safety Bill is (draft) legislation…


How Microsoft Will Block Macros To Stop Malware
Microsoft recently announced that it will be blocking Visual Basic for Applications (VBA) macros by default as a way to stop the spread of malware. Since these macros are important automation tools for Microsoft Office apps, how is this going…


European Oil Facilities Targeted By Cyber Attacks
In a worrying trend, oil facilities in Germany, Belgium and the Netherlands have all recently been targeted by cyber-attacks.
Germany
The attack on German oil, vehicle fuel and petroleum products company Oiltanking Deutschland GmbH &…


30% Rise In Crypto-Laundering
A report by blockchain data platform ‘Chainalysis’ has shown a 30 per cent increase in cryptocurrency being used for money laundering in 2021 compared to the previous year.
$8.6 Billion
The 2022 Crypto Crime Report noted how cybercriminals…


Study Shows No-One Is Immune From Phishing
A new report from F-Secure has revealed that the most technically competent staff are just as likely (if not more likely) to fail a phishing test exercise.
Phishing
Phishing attacks typically involve sending emails that appear to come…


How to Avoid Being “Doxxed”
In this article, we look at what doxxing is, some examples of doxxing, and what can be done to protect ourselves and our businesses from being ‘Doxxed’.
What Is Doxxing?
Doxing is a 90s hacker term meaning for dropping (personal)…


What Is A ‘Watering Hole’ Attack?
In this tech insight, we look at what a watering hole attack is, some examples of such attacks, and how businesses can defend against this threat.
Poisoning The Water
A watering hole attack is a targeted, ‘supply chain,’ cyber-attack…


How To Check Your VPN
In this article, we take a look at some of the ways users can assess how good their VPN really is.
What Is A VPN?
A ‘Virtual Private Network’ (VPN) is used to keep internet activity private, evade censorship / maintain net neutrality…


The Essentials Of A ‘BYOD’ Policy
In this article, we look at what BYOD is, why a BYOD policy is important, and what elements form the essential blueprint of a BYOD policy.
What Is BYOD?
The term Bring Your Own Device (BYOD) has been around since 2004 when it was first…


What Is A Password Manager?
In this tech insight, we look at challenges to using passwords, what password managers are, and why they are still so important.
The Limitations and Challenge of Passwords
Passwords have long provided a practical way to log in to websites,…


A Business Continuity Plan : The Essentials
In this article, we take a look at what a Business Continuity Plan is, what it should contain, and why it’s such an important document.
Preparing
Accepting that the unexpected and disasters will happen (and that you can plan how to…


Email Security
In this tech insight, we take a look at the many threats to email security that businesses face and what businesses can do to mitigate them, together with what help is available to help tackle those threats effectively.
Email Accounts For…


GoDaddy “Security Incident” Could Affect 1.2 Million
In this week’s security update, GoDaddy has reported a hack/data-breach on its managed WordPress hosting service which could mean that the details of 1.2 million users may have been exposed. Reports indicate that an intruder gained access…


One-Third Of UK Employees Being Remotely Monitored By The Boss
A Prospect trade union poll has revealed that 32 per cent of UK workers are being remotely monitored and tracked by employers.
Big Rise
The poll also shows a rise in the number of employees under remote surveillance that’s up from a…


Tech Insight : WAP … WEP … What ???
In this tech insight, we take a brief look at the WEP and WAP security protocols, and what happened to them.
What Is WAP?
Developed by Ericsson, Motorola, Nokia, and Unwired Planet, and introduced back in 1999, Wireless Application Protocol…


Crypto ATM Scammers
An FBI announcement has warned that scammers are now directing victims to use physical cryptocurrency ATMs and digital QR codes to complete payment transactions.
What Are Cryptocurrency ATMs?
A cryptocurrency ATM is a physical kiosk/terminal/device…


One Million UK households May Be ‘Brushing’ Scam Victims
A report from Consumer watchdog Which? reveals that as many as 1.1 million people in the UK may have been caught up in a parcel delivery ‘brushing’ scam.
What Is Brushing?
Brushing is where people are sent packages of goods to their…


Massive Rise In HTTPS Attacks
The latest “ThreatLabz: The State of Encrypted Attacks,” 2021 report has shown a 300 per cent increase in online attackers using HTTPS to cloak their activities and blend in with other traffic.
HTTPS
HTTPS, the encrypted version of…


Scam Calls : A Significant Update
This week, we heard the good news that the big phone networks have agreed to automatically block foreign scam calls, and we heard the bad news that an Ofcom survey has revealed that 45 million people in the UK were targeted by scam text messages…


30 Countries Pledge To Act On Ransomware
The international Counter-Ransomware members from 30 countries have issued a joint statement outlining their intent to take action to counter the growing threat posed by ransomware.
What Is Ransomware?
Ransomware is a form of malware…


How To Tell If You’re Being Spoofed
Many cybers attacks now take the form of using fake/spoof communication to trick victims into parting with personal (or company) data, or money. We take a look at some of the most popular and widely reported methods and how to avoid falling…


Proposed Ban For Mass Facial Recognition & ‘Predictive’ Policing
The European Parliament has adopted a resolution calling for a ban on the use of AI-based predictive policing systems and the processing of biometric data that leads to mass surveillance.
Areas
The resolution seeks to ban the use of facial…


Domain Security
After a recent report found that poor domain security has left most Global 2000 companies vulnerable to the threats of phishing and brand abuse, we take a closer look at domain security and how businesses can maximise their protection against…


QR Codes … A Security Risk?
In this tech-insight, we take a look at what QR codes are used for, review some well-known security risks, and outline what action you can take to protect yourself from malicious QR codes.
Quick Response (QR) Codes
A QR code is a machine-readable…


Amazon To Start Selling Cyber Insurance
Amazon has entered the B2B insurance market through a partnership with Superscript and is offering cyber insurance to small and medium-sized businesses in the UK.
Cyber Insurance?
Cyber insurance protects businesses (and individuals providing…


No More Passwords For Microsoft Logins
In a bold step, Microsoft has announced that it is getting rid of all password logins, and that users will have to use an authenticator app or other solution instead.
Vision
Back in 2019, Microsoft announced that 100 million people were…


Apple Issues Patch To Stop iPhone ‘Zero-Click’ Spyware
Apple has issued a security update following the discovery of a zero-day, zero-click “spyware” that could infect iPhones and iPads.
Discovered By Researchers
The threat was discovered by independent researchers from the University…


Tech-Insight : What Is ‘Doxing’ ?
In this article, we look at what doxing is, the legality of it, some examples of doxing, and we consider what we can do to protect ourselves and our businesses from attack.
What Is Doxing?
Doxing is a term meaning for dropping (personal)…


What Is Most Web Traffic Made Up Of?
In this article, we look at how a surprisingly large proportion of Internet traffic is made up of bots, how many of these can be ‘bad bots’, and what businesses can do to keep enjoying the benefits of good bots while guarding against the…



Tech News # 1 : Biometrics Could Assist the Taliban
Human Rights groups fear that the Taliban could soon be able to use collected biometric data to identify contractors and locals working with the US military.
What Biometric Data?
It has been reported that, over time, while on operations…


Tech Insight : How (Simple) 2FA is Being Beaten
In this article, we take a look at how two-factor authentication, introduced to help add an extra layer of security to logins, has its own vulnerabilities.
What Is 2FA?
Two-factor authentication (2FA) combines a username and password…


Delivery Scams Top The ‘Smishing’ List
Data, published by trade association UK Finance for security provider Proofpoint, shows that parcel and package delivery scams are now the most common form of ‘smishing’ attempts.
What Is Smishing?
Smishing is where an attacker sends…


Crypto Hackers Return Most Of The $610 Million Crypto Cash
On 12 August, the Poly Network DeFi platform announced that, following the theft of $610 Million in digital coins, the hacker thieves had returned $342 million. However, it’s been reported that more recently, almost all of the stolen crypto…


Tech Insight: What Is Zero Trust?
With mobile computing, software-as-a-service (SaaS), and now remote working moving the focus of IT security away from the traditional perimeter, this article takes a brief look at what a ‘Zero Trust’ approach is and how it can help.
More…


Tech Insight – What Is 2FA?
Two-Factor-Authentication (2FA) refers to another piece of information that users are required to provide (in addition to username and password login details) to access a website/platform/account. Requiring another piece of information protects…


Doesn’t Microsoft Back-Up Your Stuff? Er, No!
Recognising that Microsoft 365 does not comprehensively back up your data means that making sure that you have a third-party, “point-in-time” backup solution is an important consideration for your business.
Only For 30 Days
Microsoft…


Tech Insight – What Is A VPN?
In this article, we take a brief look at what a VPN is, how it works, its advantages, plus its disadvantages.
What Is A VPN?
A Virtual Private Network (VPN) is a service that allows you to create a secure connection to another network…



How Secure Is Your Software/Digital Supply Chain?
It is easy to think that cyber-attacks are likely to come from outsiders unconnected to the business, but how much do you know about the security of your digital supply chain?
Software Supply Chain Risks
Businesses use many different…


Guarding Against The Rise In Router and VoIP Attacks
After a recent high profile media story highlighted how poor router security led to a police raid of the home of an innocent family, we take a look at how Wi-Fi piggybacking attacks against home and domestic targets, and VoIP hacking of businesses…


Get Notified By Google If Your Passwords Are Compromised
As part of Google’s latest security updates to Chrome and Android, users will not only be alerted if any of the passwords in their Password manager are compromised but will also be given the opportunity to make a quick fix.
Quick Fix –…



New Privacy Features For Android 12
Google has announced the release of the first beta of Android 12 which has a range of new features including some security measures which Google hopes can match those of Apple.
Design Change
Announced recently at a developer conference,…


The Issue of Push Payment Fraud Reimbursement
With Barclays Bank recently publishing the figures of refunds it made to customers who fell victim to authorised push payment (APP) fraud, there have been calls for greater transparency and reform to the current (voluntary) reimbursement code.
Authorised…



Tech Insight: What Are Firewalls?
In this article, we take a brief look at what a firewall is, what types there are, and the benefits and drawbacks of firewalls.
Firewall
A firewall is a network security system that can monitor and control incoming and outgoing network…


Tech Insight: What Is Patching or Patch Management?
In this article, we take a brief look at the importance of patch management in maintaining security.
Patches and Patch Management
Patches are the software fixes for known security vulnerabilities in software such as operating systems,…


Google Users To Be Auto-Enrolled In Two-step Verification
In a recent blog post, Google has announced that the automatic enrolment of Google account users in Two Step Verification ‘2SV’ is coming soon.
Passwords – Single Biggest Threat To Online Security
In the blog post on ‘On World…


Old Router Risks Could Affect Millions
An investigation by consumer watchdog ‘Which?’ has highlighted how millions of people around the UK are using old routers with security flaws.
The Investigation
The Which? investigation surveyed 6,000 UK adults and, with the help…


How To Browse Privately
This article takes a brief look at what private browsing actually means with popular browsers and software, and how genuinely private browsing could be achieved.
Why Browse Privately?
Over 80 percent of websites use one or more tracking…



MI5 ‘Think before You Link’ Campaign Warning To Staff
MI5 is using a ‘Think before You Link’ campaign to warn its workers about the growing threat of being targeted for information by actors for hostile states using fake profiles on platforms such as LinkedIn.
Think before You Link
It…


Russia Sanctioned Over Cyber Attacks
President Biden’s administration in the U.S. has placed new sanctions on Russia over alleged cyberattacks affecting the U.S. and its allies.
What Is Russia Accused Of?
The U.S. government sanctions relate to:
The ‘SolarWinds attack’…


Ransomware Payouts Tripled Last Year
The Ransomware Threat Report 2021 from Unit 42 shows that the average amount paid by ransomware victims tripled from 2019 to 2020.
Ransomware
Ransomware is a form of malware that encrypts the important files on a computer and the user…


Are Macs More Secure Than PCs?
Apple Macs have long had a reputation for being more secure than PCs but where does this idea come from and is it really the case?
How Did It Start?
Apple itself supported the idea that Macs didn’t get computer viruses until (in 2012)…


Two ISPs Helped Secret Government Web Spying
Using the Investigatory Powers Act of 2016, it has been reported that a recent government test of tracking users' web histories has been helped by two ISPs.
The Investigatory Powers Act
The Investigatory Powers Act 2016 (also known as…


Google Alerts Used In Malware Scam
It has been reported that hackers have been able to spread malware using fake news stories via the Google Alerts service.
Google Alerts
Launched in 2003, Google Alerts is Google’s content change detection and notification service which…


Post Office Biometric Authentication
The Post Office has announced that its new, free app will include the latest biometric-face matching and liveness biometric authentication.
Partnership With Yoti
As a result of a partnership with London-based digital identity company,…


Emotet : A Million Bucks per Incident
In the light of a reported recent victory by Europol in trying to stop the particularly dangerous Emotet malware, we look at what it is, how it is spread, and how to try and guard against it.
What is Emotet?
Emotet is a computer malware…


What Is Zero Trust?
With mobile computing, software-as-a-service (SaaS), and now remote working moving the focus of IT security away from the traditional perimeter, this article looks at what a Zero Trust approach is and how it can help.
More Complex Demands
The…


Data About You Held By UK Government
In this article, we look at not just the story of how a staggering 400,000 police records were accidentally deleted but also at the wider picture of what information is held about us UK citizens by the authorities, and what powers we have over…


Microsoft’s Password Manager Works Across Devices and Browsers
Microsoft has announced that its new Authenticator App will also work as a password manager which will allow passwords to be synced across desktop and mobile devices (iOS and Android) as well as Edge and Google Chrome browsers.
Free Authenticator
The…


Personal Data Security Given Low Priority By Christmas Online Shoppers
A survey commissioned by PCI Pal® shows that Christmas online shoppers appear to be more concerned about prices and the speed and cost of deliveries than the security of their personal data.
Priority Ranking
The survey asked 2,002…


Stay Safe Online This Christmas
With Christmas just around the corner here are some suggestions for how you and your loved ones can stay safe online over this festive period and beyond.
The Shift Online
The pandemic has prompted a huge shift online this year for work…


UK COVID Vaccine Maker Targeted By Suspected North Korean Hack
It has been reported that UK drug company AstraZeneca has been targeted by suspected North Korean hackers thought to be looking for COVID vaccine secrets.
Used WhatsApp and LinkedIn
Over the last few weeks, attacks have reportedly been…


HMRC Self Assessment Scam Warning
HMRC has issued a warning to those completing Self Assessment tax returns for 31 January not to be caught out by SMS messages and email scams purporting to be from HMRC.
Bogus
An upturn in scams using HMRC’s name has meant that in the…


The Difference Between Cloud Backup and Cloud Storage
This article looks at the difference between cloud backup and cloud storage and how each contributes to daily business life; business continuity and disaster recovery.
The Need For Storage
Businesses not only have limited hard drive space,…


Data Breaches : The Fallout
Data Breaches
A personal data breach, as defined by the UK’s data watchdog and regulator, The Information Commissioner’s Office (ICO), is “a breach of security leading to the accidental or unlawful destruction, loss, alteration,…


Scammer Accidentally Calls Cyber-Crime Squad
A hapless scammer pretending to be from a broadband network got more than he bargained for when he accidentally called (and tried to work his scam) on the cyber-crime squad of an Australian police force.
Claimed To Be From Broadband Network
The…


Bring Your Own Device (BYOD)
In this article, we look at why bring your own device (BYOD) is still popular and we look at some of the risks businesses face by allowing BYOD.
BYOD
BYOD has been around since 2004 and essentially allows employees to bring in their personally…


How Do You Know If Your Website Has Been Hacked?
Hacking of websites, as well as devices and accounts, is all too common and this article looks at some of the tell-tale signs that your website may have been hacked, and what to do about it.
Signs
The kinds of signs that alert website…


Password Security and The Road Ahead
The fact that websites continue to be hacked and passwords are frequently stolen (and that a computer recently set a record by guessing 100 billion passwords per second) calls in to question how passwords can still be used safely and what lies…


Tech Increasing Domestic Abuse
With domestic abuse on the rise, particularly since the pandemic lockdowns, we look at some of the chilling ways that smart devices and other technology are being used as a tool by abusers.
Rise In Reports
A BBC Panorama and Women’s…


Learning From the WisePay Attack
In the wake of the recent attack on the WisePay website which saw some parents unwittingly making school payments to cyber-criminals, we look at how to spot whether personal data may have been compromised and how to protect personal information…


Are You Being Tracked By WhatsApp Apps?
A recent Business Insider Report has highlighted how third-party apps may be exposing some data and details of the activity of WhatsApp users.
WhatsApp – Known For Encryption
Facebook-owned WhatsApp is known for its end-to-end encryption. …


Facial Recognition, Facial Authentication and the Future
Facial Recognition and facial authentication sound similar but there are distinct differences and this article takes a broad a look at how both are playing more of a role in our lives going forward. So firstly, what's the difference?
Facial…
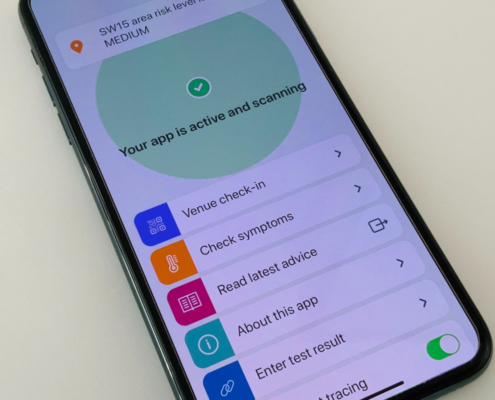

Privacy Campaigners Challenge Government Over Test and Trace
Privacy campaign groups Big Brother Watch and The Open Rights Group have voiced their concerns that there is a lack of clarity from the government about how the data of users of the new NHS contact tracing app will be protected.
Concerns
The…


Cybersecurity Top of List for Digital Transformation
A recent survey appears to have shown that changes brought by the pandemic have meant that IT buyers from companies working on digital transformation now value cybersecurity the most.
Survey
The survey, conducted among IT business leaders…


The Challenge of User Access Permissions
Employees being given too much access to privileged, sensitive company data can put an organisation in danger. In this article, we explore the issues around this subject and how businesses can minimise the risk.
Survey
In a recent…


Tips & Tools To Keep Kids Safe Online
The online environment can be a dangerous as well as a fun place for young people so here are some tips and tools to help keep kids safe online.
The Risks
Children face many risks online including seeing/watching things they shouldn’t,…



Making Your Router Secure
With your router in charge of all incoming and outgoing Internet traffic and controlling the Wi-Fi network for your devices, it makes sense to make it as secure as possible.
Routers
Your router is the device that connects your computer…


Lockdown Love Scams
Details emerged this week of a scam whereby a man claiming to be on a top-secret military mission contacted a lady on a dating site and encouraged her to switch to an encrypted message service in order to steal money and personal details.
Hooked
In…


Ritz Roasted
Some diners with bookings at the Ritz Hotel were reportedly targeted by phone scammers who posed as hotel staff to steal credit card details.
What Happened?
The ID spoofing attack involved the fraudsters pretending to be hotel staff,…


Celebrity Twitter Accounts Hacked For Bitcoin
Twitter accounts of celebrities including Barack Obama and Bill Gates were hacked and used to operate a scam, asking people to donate bitcoin.
What Happened?
Hackers used the tools that were normally only available to Twitter staff to…


LinkedIn Sued Over Clipboard-Reading Allegations
An Apple iPhone user in the U.S. has sued LinkedIn over allegations that its app was reading the contents of an Apple device user’s clipboard without their knowledge.
Spying Complaint
The complainant, Adam Bauer, alleges that LinkedIn’s…


Free Cybersecurity Testing Module For Remote Workers
A new penetration testing module as part of the National Cyber Security Centre’s Exercise in a Box toolkit will help remote workers of SME’s to improve their cybersecurity. The free cybersecurity testing module for remote workers is the…


Police Crack Encrypted Network To Reach Crime Gangs
An international law enforcement operation has led to the cracking of the EncroChat Android phone network and the arrest of criminal gangs.
The Network
The France-based EncroChat network, which was discovered by the French National…


NatWest’s Extra Layer of Behavioural Biometrics Security
In partnership with Visa, NatWest has added an invisible layer of behavioural biometrics as part of an authentication process that will enable compliance with a new EU regulation.
Which Regulation?
The Strong Customer Authentication (SCA) regulation,…


Beware of Fake Contact Tracer Messages
Just as you thought that cybercriminals had exploited every aspect of the pandemic, there are now warnings to beware of fake contact tracer messages.
Contact Tracing in the UK
Here in the UK, NHS contact tracers are now contacting…


What Is Vishing? And How to Guard Against It
‘Vishing’, or ‘phishing over the phone’ is on the rise and in this article, we look at what vishing is, and the techniques used. We show examples and explain how to guard against it.
What Is Vishing?
The word Vishing is a combination…


eBay Port Scanning Causes Alarm
Reports that eBay has been running port scans against the computers of visitors to the platform have caused alarm over potential security issues.
Port Scans
Port scanning is something that many people associate with cyberattacks…


Does My Phone Have A Virus?
Have you have ever wondered "does my phone have a virus?", if so read on. This article looks at how to tell if your phone has a virus, what to do if you think it has, and how to protect your phone. Phones are essentially powerful mobile computers…


Robotic Dog Maintains Social Distancing in Singapore
A robotic dog maintains social distancing in a trial in a park in Singapore. The robot called SPOT warns visitors to observe social distancing measures.
Sign
The 2-week trial in Singapore’s Bishan-Ang Mo Kio Park is a collaboration…


Scam Warnings For Remote Workers
More scam warnings for Zoom, Teams and Meet users as reports show hackers still use domains related to popular collaborative platforms to target remote workers with phishing scams during lockdown.
Domains
Almost as soon as the lockdown…


How Tech is Helping Reduce Lockdown Stress and Mental Health Problems
A state of lockdown has increased our reliance on technology to help us meet our needs and to reduce our stress.
Here are some of the many ways that technology has helped us to look after our mental health in these challenging times.
Apps…


Apple and Google Ban Location Tracking in Contact Tracing App
Apple Inc and Alphabet Inc (Google) have both announced that they will not use GPS location tracking as part of the COVID-19 contact tracing app that they are jointly developing.
Contact Tracing Apps
With contact-tracing and testing believed…


Businesses Get Extra Time To Meet New Secure Payment Processing Rules
The Financial Conduct Authority (FCA) has given UK businesses an extra 6 months to reach compliance with the new Strong Customer Authentication (SCA) rules for secure payment processing.
What Are the SCA Secure Payment Processing Rules?
The…


How To Securely Dispose of Old Phones, PC’s and Laptops
When our PCs, laptops, phones, and other devices need to be replaced, disposing of them in a way that does not pose a data security risk is especially important. Here are some tips on how to dispose of devices securely.
Backup
Before…
























































































Google Blocks 18 Million Coronavirus Scam Emails Per Day
Google is reported to have been blocking 100 million phishing emails per day and 18 million email scams relating specifically to coronavirus.
Millions of Scams and Spam Messages Daily
On its Cloud blog on 16th April, Google reported that…
























































































Data Reveals Business Worries About Remote Working Challenges
London-based security company Redscan has reported that recent Google searches reveal how businesses are focused on how they can adapt to the security and technology challenges posed by remote working.
Not Prepared
This does appear to…
























































































Maintaining Security on Employee Exit
When employees leave (or are asked to leave) or retire from businesses and organisations, those entities still have a legal responsibility to ensure that security levels are maintained with regards to data security.
Laws For Data
The…
























































































Research Indicates Zoom Is Being Targeted By Cybercriminals
With many people working from home due to coronavirus, research by Check Point indicates that cybercriminals may be targeting the video conferencing app ‘Zoom’.
Domains
Cybersecurity company ‘Check Point’ reports witnessing a…
























































































Cybercriminals Hijacking Netflix and Other Streaming Accounts
It has been reported that the surge in the use of streaming music and video services has been accompanied by a surge in the number of user accounts being taken over by cybercriminals.
Entertainment During Isolation
Self-isolation and…
























































































Maintaining Security During The COVID-19 Health Crisis
The current global health crisis may bring many different IT security challenges to businesses and organisations and this article highlights some of the ways that you can prepare to keep IT security covered as best you can at this difficult…
























































































Cybercriminals Take Advantage of Covid-19 Outbreak With Phishing Emails
Some cybercriminals have already taken advantage of the fear surrounding the Covid-19 outbreak by sending out phishing emails that promise cures, seek donations, or heighten panic in order to extract personal data and money.
Phishing For…
























































































Billions Of Devices At Risk Due To Wi-Fi Chip Vulnerability
A security threat to devices, Wi-Fi access points (APs), and routers that comes from the Kr00k Wi-Fi chip vulnerability could affect billions according to security researchers.
Kr00k
The existence of Kr00k, also known by the catchy name…
























IT Security Updates issue 23
Redcar Council Victim
Of Major Ransomware Cyber Attack
A Northern England
Borough Council has been reduced to using pen and paper to deliver key
services. Redcar and Cleveland Borough Council has struggled to counter a
Ransomware attack…
























































































Google Indexing Makes WhatsApp Group Links Visible
A journalist has reported on Twitter that WhatsApp groups may not be as secure as users think because the "Invite to Group via Link" feature allows groups to be indexed by Google, thereby making them available across the Internet.
Links…
























































































Worries About Huawei Persist
Security fears about Huawei products being used in the new 5G networks are still being expressed by the Trump administration, while Google has clarified its position on the matter.
What’s So Bad About Huawei?
Back in July 2018, …
























































































Growth in Threats To Apple Compared To Windows Machines
In a trend that appears contrary to popular perceptions, the latest Malwarebytes (annual) State of malware report has revealed that the growth in attacks on Apple endpoints is outpacing the threats targeting Windows machines.
11…
























































































Police Images of Serious Offenders Reportedly Shared With Private Landlord For Facial Recognition Trial
There have been calls for government intervention after it was alleged that South Yorkshire Police shared its images of serious offenders with a private landlord (Meadowhall shopping centre in Sheffield) as part of a live facial recognition…
























































































Avast Anti-Virus Is To Close Subsidiary Jumpshot After Browsing Data Selling Privacy Concerns
Avast, the Anti-virus company, has announced that it will not be providing any more data to, and will be commencing “a wind down” of its subsidiary Jumpshot Inc after a report that it was selling supposedly anonymised data to advertiser…
























































































‘Snake’ Ransomware, A Threat To Your Whole Network
Over the last couple of weeks, there have been reports of a new type of ransomware known as ‘Snake’ which can encrypt all the files stored on your computer network and on all the connected devices.
Discovered
Snake ransomware is so-called…
























































































Email Security (Part 2)
Following on from last weeks’s featured article about email security (part 1), in part 2 we focus on many of the email security and threat predictions for this year and for the near, foreseeable future.
Looking Forward
In part 1 of…
























































































Email Security (Part 1)
In this week's featured article, which is the first of two parts on what is a huge subject for businesses to tackle, we take a look at some of the important issues of email security and how businesses can try to strengthen this crucial area…
























































































New Phishing Tracker For Office 365
Microsoft is launching a new "campaign views" tool in Office 365 that is designed to offer greater protection from phishing attacks by enabling businesses to be able to spot the pattern of a phishing campaign over individual messages.
Context…
























































































Exploring Encryption
Encryption comes from the age-old science of cryptography. In the digital world of today, encryption refers to using electronic devices to generate unique encryption algorithms which essentially scramble messages and data, making them…
























































































The Difference Between Backup and Disaster Recovery
We’re all familiar with the value of making a backup of business data, but how does this fit with ‘Disaster Recovery’ and ‘Business Continuity’ strategies? This article takes a brief look at how these elements fit together to…
























































































Hacker’s Website Closed Down In International Operation
A website (and its supporting infrastructure) which sold a variety of hacking tools to other would-be cybercriminals has been closed down after an investigation by agencies from multiple countries including the UK's National Crime Agency (NCA).
IM-RAT
The…
























































































Google Or Samsung Android Cameras Could Be Spying On You
Researchers at Checkmarx say they have discovered vulnerabilities in Google and Samsung smartphone apps that could allow hackers to remotely spy on users, using their phone’s camera and speakers.
Study
The proof-of-concept (PoC) study…


Don’t let Black Friday become an actual black Friday! It’s Holiday Season for the bad guys too!
Shopping
online is appealing, not only do you save time avoiding trying to park in a
full car park, or queuing to pay in crowded, and very hot store, but you do
need to navigate an increasingly dangerous cybersecurity minefield. It's…
























































































Despite Patches, Researchers Warn That Intel Chips Are Still Vulnerable
The New York Times has reported that despite Intel issuing patches for security flaws (that were discovered last year) in its processors, security researchers are alleging that the processors still have some serious vulnerabilities.
What…
























































































Research Says Memes Can Tell Between Humans and Bots
Researchers from the University of Delaware have concluded that when it comes to authentication for logins, Memes may be one of the strongest techniques to distinguish between a human and a bot.
The Bot Challenge
One of the great challenges…
























IT Security Updates issue 22
The latest news from the sector finds worrying Amazon’s IoT technologies with big cyber security flaws, could Microsoft be in trouble thanks to GDPR, and is Simjacking the next big cyber security threat?
Ring Doorbell Tech
Leaves Door…
























































































Office 365 Voicemail Phishing Scam Warning
Security company McAfee has reported observing a phishing scam which uses a fake voicemail message to lure victims into entering their Office 365 email credentials into a phishing page.
How The Attack Works
According to McAfee’s blog,…
























































































“Stalkerware” Partner-Spying Software Use Rises By 35% In One Year
Kaspersky researchers have reported a 35 per cent rise in the number of people who have encountered the use of so-called ‘stalkerware’ or ‘spouseware’ software in the first 8 months of this year.
What is Stalkerware?
Stalkerware…
























































































Amazon Echo and Google Home ‘Smart Spies’
Berlin-based Security Research Labs (SRL) discovered possible hacking flaws in Amazon Echo (Alexa) and Google Home speakers and installed their own voice applications to demonstrate hacks on both device platforms that turned the assistants…
























































































Banking App Fraud On The Rise
A recent report from cyber-security company RSA has highlighted a significant rise in fraud via fake banking apps.
Number of Attacks Has Trebled
The Fraud and Risk Intelligence (FRI) team at RSA have noted a tripling of the number of…
























































































Any Thumbprint Unlocks a Galaxy A10
Also, the lawsuit alleges that Equifax relied upon the username “admin” and the password “admin” to protect a portal used to manage credit disputes, thereby making it incredibly easy for any hackers to guess. For example, many…
























































































Equifax Hack Inevitable Says Lawsuit
A lawsuit against US Credit Rating Company Equifax relating to the massive 2017 hack alleges that the breaching of Equifax’s systems was “inevitable because of systemic organisational disregard for cybersecurity and cyber-hygiene best practices.”
What…
























IT Security Updates issue 21
The latest news finds
the Cookie ‘Monster’ attacking Sesame Street’s Online Webstore, FIFA 20 has had
a major user data breach, spoofing emails are becoming more and more elaborate
and costing companies millions, and more …
Cookie…
























































































Ex-Employee Claims Your G Suite Data Is Not Encrypted
A report by a former Google
employee on the ‘Freedom of the Press Foundation’ website warns organisations that any data stored
on Google’s G Suite is not encrypted, can be accessed by administrators and can be shared with law
enforcement…
























































































Food Writer Loses £5,000 in Phone ‘Simjacking’
Well known food writer, Jack Monroe, has reported falling victim to criminals who were able to steal £5,000 from her bank and payment accounts in a "Simjacking” attack.
What Is Simjacking?
Simjacking, simswapping or ‘phone hijacking’…
























































































Local Authorities Facing 800 Cyber Attacks Per Hour
Figures gathered by insurance broker Gallagher - through the Freedom of Information (FoI) Act - have shown that UK local authorities were hit by an average of 800 cyber-attacks every hour in the first six months of this year.
Problem…
























































































Google’s Chrome To Block Mixed Content Pages Without HTTPS
Google has announced that in a series of steps starting in Chrome 79, all mixed content will gradually be blocked by default.
What Is Mixed Content?
Mixed content refers to the insecure http:// sub-resources that load into https://…
























































































Worldwide Rollout of ‘Personal Vault’ OneDrive Security Features
Microsoft has announced that the ‘Personal Vault’ security features for its OneDrive storage service are now available worldwide on all OneDrive consumer accounts.
What Is Personal Vault?
Personal Vault is a protected area in…
























































































People Who Broke Into Courthouse Claim It Was Part of Assessment
Two security specialists who performed a physical break-in on the US courthouse that hired their company for a penetration test have claimed that their break-in was part of their assessment of security.
What Happened?
Dallas' State Court…
























































































IBM To Offer Largest Quantum Computer Available
IBM has announced that it is opening a Quantum Computation Centre in New York which will bring the world's largest fleet of quantum computing systems online, including the new 53-Qubit Quantum System for broad use in the cloud.
Largest Universal…
























































































Joker Malware Found In 24 Apps In Google Play Store
Security researcher Aleksejs Kuprins of CSIS cybersecurity services company has discovered 24 apps which have been available for download in the Google Play Store that contain ‘Joker’ malware.
What Is Joker Malware?
Joker malware…
























































































AI Mimics CEO’s Voice To Steal £201,000
A recent Wall Street Journal report has highlighted how, in March this year, a group of hackers were able to use AI software to mimic an energy company CEO’s voice in order to steal £201,000.
What Happened?
Reports indicate that the…
























































































Report Shows That 99% of Cyber Attacks Now Involve Social Engineering
The Human Factor report from Proofpoint shows that almost all cyber-attacks, at some stage, involve the exploitation of human error in the form of social engineering.
What Are Social Engineering Attacks?
Social engineering attacks…
























































































Leaving Your Job? Don’t Take Personal Data With You Warns ICO
The Information Commissioner’s Office (ICO) has warned those retiring or taking a new job that under the Data Protection Act 2018, employees can face regulatory action if they are found to have retained information collected as part of their…
























































































Student Textbooks Malware Threat
Kaspersky’s blog is warning students who are about to go back after the summer holidays to beware of the risk of malware that’s masked as textbooks and essays online.
Students Targeted
According to Kaspersky, K-12 and college students…
























IT Security Updates issue 20
The latest news from the sector sees two major flaws highlighted by cyber security professionals with major implications for enterprise-level IT patch management cycles, BioStar 2 users face uncertainty over flaw and more ...
South Korean…
























































































Your Password Can Be Guessed By An App Listening To Your Keystrokes
Researchers from SMU’s (Southern Methodist University) Darwin Deason Institute for Cyber-security have found that the sound waves produced when we type on a computer keyboard can be picked up by a smartphone and a skilled hacker could…
























































































Over A Million Fingerprints Exposed In Data Breach
It has been reported that more than one million fingerprints have been exposed online by biometric security firm Suprema which appears to have installed its standard Biostar 2 product on an open network.
Suprema and Biostar 2
Suprema…
























































































Facial Recognition at King’s Cross Prompts ICO Investigation
The UK’s data protection watchdog (the Information Commissioner’s Office i.e. the ICO) has said that it will be investigating the use of facial recognition cameras at King’s Cross by Property Development Company Argent.
What…
























































































Is Your Website Sending Scammers’ Emails?
Research by Kaspersky Labs has discovered that cyber-criminals are now hijacking and using the confirmation emails from registration, subscription and feedback forms of legitimate company websites to distribute phishing links and spam content.
How?
Kaspersky…
























































































$1 Million Bounty For Finding iPhone Security Flaws
Apple Inc recently announced at the annual Black Hat security conference in Las Vegas that it is offering security researchers rewards of up to $1 million if they can detect security flaws its iPhones.
Change
This move marks a change…
























































































One-Third of Major VPNs Owned By Chinese
A recent survey by VPNpro has revealed that almost one-third of the most popular VPN services are secretly owned by Chinese companies that may be subject to weak privacy laws.
VPN
A ‘Virtual Private Network’ (VPN) is used to keep…
























































































Vulnerability in Contactless Card Allows Bypassing of £30 Limit
Researchers from security
company Positive Technologies have reported found a vulnerability in Visa contactless cards that
could lead to your bank account being drained if your card fell into the wrong hands.
Device
The researchers…
























































































Commercial Release of BlueKeep Malware Causes Concern
Tech and security commentators have expressed their fears that a version of the BlueKeep malware (that’s been included in a commercial penetration testing toolkit) could prove to be dangerous if it falls into the wrong hands.
What Is BlueKeep?
BlueKeep…
























































































Lancaster University Hit By “Sophisticated and Malicious Phishing Attack”
Lancaster University, which offers a GCHQ accredited cyber-security course and has its own Cyber Security Research Centre has been hit by what it has described as a "sophisticated and malicious phishing attack”, resulting in the leak of the…
























































































Security Flaw Discovered In NHS Anaesthetic Machines
Cybersecurity firm CyberMDX has reported the discovery of a security flaw in some Internet-connected GE Healthcare anaesthetic machines which could leave them vulnerable to hacks.
Security Flaw
The security flaw has been described as…
























































































Facial Recognition Glasses For Covert Surveillance
The “iFalcon Face Control” AR glasses that incorporate an 8-megapixel camera in the frame and NNTC facial recognition technology (due to go on sale next year) are reported to have already been deployed into several security operations.
US…
























































































Samsung’s Advice To Virus-Check TVs Causes Customer Concern
Samsung’s recent release of a how-to virus check video coupled with the advice to complete the check “every few weeks” has caused confusion and concern among customers.
Video
At the heart of Samsung’s virus-checking information…
























IT Security Updates issue 19
The latest news from the sector sees Malware on a laptop become “art”, Microsoft in trouble with the NSA thanks to WinXP vulnerabilities, Dark Net police crackdowns driving cyber criminals into encrypted chat spaces – like Telegram and more…
























































































SurveyMonkey’s Bold Dublin Move
California-based online survey software company SurveyMonkey has opened a datacentre in Dublin with a view to attracting enterprise customers in the EMEA region.
SurveyMonkey
SurveyMonkey, which was established in Portland by Ryan and…
























































































Old Routers Are Targets For Hackers
Internet security experts are warning that old routers are targets for cyber-criminals who find them an easy hacking option.
How Big Is The Threat?
Trend Micros have reported that back in 2016 there were five families of threats for routers,…
























































































3D Shopping Via Google Search
Later this month, Google will be rolling out 3D Augmented Reality (AR) in its search results, a change which could allow retailers to show their products online in a way that enables customers to a virtually ‘try’ those products and see…
























































































Proposed Legislation To Make IoT Devices More Secure
Digital Minister Margot James has proposed the introduction of legislation that could make internet-connected gadgets less vulnerable to attacks by hackers.
What’s The Problem?
Gartner predicts that there will be 14.2 billion ‘smart’,…
























































































G7 Cyber Attack Simulation To Test Financial Sector
The G7 nations will be holding a simulated cyber-attack this month to test the possible effects of a serious malware infection on the financial sector.
France
The attack simulation was organised by the French central bank under France’s…
























































































Data Breach Report A Sharp Reminder of GDPR
The findings of Verizon’s 2019 Data Breach Investigations Report have reminded companies that let customer information go astray that they could be facing big fines and damaging publicity.
The Report
The annual Verizon Data Breach Investigations…
























IT Security Updates issue 18
The latest news from the sector sees HMRC fall foul of GDPR rules on biometric data content, Dell and Sierra Wireless rush out patches to fix flaw issues, farming businesses now targeted by cyber criminals, new rules on IoT hardware being devised…
























































































Microsoft’s Move Away From Passwords Towards Biometrics
In a recent interview with CBNC, Microsoft’s Corporate Vice President and Chief Information Officer Bret Arsenault signalled the corporation’s move away from passwords on their own as a means of authentication towards (biometrics) and a…
























































































Fake Finger Fools Fool Proof Phone
A Reddit user claims to have used a 3D printer to clone a fingerprint and then use the fake fingerprint to beat the in-display fingerprint reader on a Samsung Galaxy S10.
Fingerprint Scanner
The Galaxy S10 and S10+ phone models have an…
























IT Security Updates issue 17
The latest news from the sector sees Bounty UK fined £400,000 from the ICO, NCSC launch a venture capital drive for new cyber security start-ups, this month’s patch Tuesday updates …
New Mums Service
Bounty Fined £400,000 For Unlawfully…
























IT Security Updates issue 16
The latest news from
the sector finds the ICO fining companies big sums of money for spamming and
falling foul of data privacy rules, Huawei is a big risk but how big a risk for
your business(?), how ethical hackers are helping UK universities…
























































































Fingerprint Bank Card
RBS is reportedly about to hold trials of a new, more secure biometric bank card where customers can use their fingerprint instead of a PIN to verify purchases.
April
The trial, which will involve some 200 RBS and NatWest UK-based customers, is…
























IT Security Updates issue 15
The latest news from the sector sees the ICO fine a sacked council employee for using privileged access to help his girlfriend find a job, GCHQ is getting worried about the use of Chinese “tech” in big infrastructure, the latest on Microsoft’s…
























IT Security Updates issue 14
The latest news from the sector sees Gartner identify a big increase in biometric tech spending but warns companies there are risks involved. You possibly missed Safer Internet Day 2019 but you should take a minute to learn more about the event.…
























IT Security Updates issue 13
In this edition we find why Magnacrest Ltd were charged by the ICO for failing to reply to a Subject Access Request, why your company needs to pay the Data Protection Fee if it is a data controller, ICO announce more Brexit-related data protection…
























































































Research Reveals Top-Selling Car Keyless Theft Risk
Research by consumer Group Which? has revealed that hundreds of popular models of car are vulnerable to “keyless theft”.
Keyless Car Theft
Keyless car entry systems enable owners to unlock the doors of their car with the brush of…
























IT Security Updates issue 12
In this edition we find Gartner’s latest cyber-security awareness-building idea, the Centre for Internet Security’s top three ‘threat’ trends for 2019, Cambridge Analytica’s latest woes at the hands of the ICO, how even a small pottery…
























































































Biggest Personal Data Breach Puts Password Effectiveness In The Spotlight
Password-based authentication has long been known to be less secure than other methods such as multi-step verification or biometrics, but a massive leak of a staggering 87GB of 772.9 million emails, 21.2 million passwords and 1.1 billion email…
























































































Contactless Card Fraud Has Doubled
The UK’s fraud reporting service, Action Fraud, has reported that contactless card fraud doubled in 2018 to £1.8m stolen compared with £711,000 in 2017.
Average Theft Amount Increased
The latest Action Fraud figures have also revealed…
























































































Smart Botnet Detection Needed
For businesses to maintain an effective cyber defense, the ability to prevent, detect and stop smart botnets in real-time is now an important consideration.
What Is A Botnet?
A botnet is a term for multiple malicious mini-programs working…
























IT Security Updates issue 11
The latest news from the sector sees Marriot Hotels fall victim for the second largest cyber attack in history, GDPR hits the news again as SMEs continue to fail to understand the scale of their data privacy responsibilities, 25% of NHS trusts…
























IT Security Updates Issue 10
The latest news from the sector sees the ICO get a criminal locked up for six months under the Computer Misuse Act, Vision Direct has been hacked which has seen nearly 7,000 customer credit card details affected by the hack, the Met Police’s…
























































































Free VPN Tools May Be Linked To China
A new investigation by Metric Labs of the top free VPN (Virtual Private Network) apps in Apple's App Store and Google Play has revealed that more than half are run by companies with Chinese ownership.
What’s A VPN?
A ‘Virtual Private Network’…
























































































MFA Lockout For Microsoft & Azure Users Causes Business Disruption
The latest multi-factor authentication (MFA) issue left users of Azure and Microsoft Office 365 unable to login to their accounts on Monday 21st, causing widespread disruption to businesses in Europe, Asia, and some parts of the US.
What Happened?
According…
























































































Facial Recognition For Border Control
It has been reported that the UK Home Office will soon be using biometric facial recognition technology in a smartphone app to match a user’s selfie against the image read from a user’s passport chip as a means of self-service identity verification…
























IT SECURITY UPDATES ISSUE 9
Hi again Jon and welcome to our latest ‘Essential IT Security Updates’ newsletter : essential reading for IT security and data protection leaders like you wanting to stay ahead of developments and news in this ever-changing sector. Feel…
























































































Fatal Security Flaws Discovered in Solid State Drives (SSDs)
Researchers from Radboud University in the Netherlands have released a paper highlighting several security flaws that they’ve discovered in SSDs which mean that data from a flash disk can recovered in more than one way, even if it’s supposedly…
























































































Adult Site Visits on Work Computer Lead to Network Infection
The extensive online porn-accessing habit of an employee of a US government department known as the US Geological Survey (USGS) is being blamed for a government computer network becoming infected with malware.
9,000 Pages
In an investigation,…
























IT security updates 8
Hi again and welcome to our latest ‘Essential IT Security Updates’ newsletter : essential reading for IT security and data protection leaders like you wanting to stay ahead of developments and news in this ever-changing sector. Feel…
























































































Businesses Turning To Zero-Trust Security Model
As a widening attack surface and evolving threats mean that organisations continue to breached despite a large security spend, many businesses are now turning to the 'zero-trust' security model.
What Is The Zero-Trust Security Model?
The Zero…
























































































New Tech Laws For AI Bots & Better Passwords
It may be no surprise to hear that California, home of Silicon Valley, has become the first state to pass laws to make AI bots 'introduce themselves' (i.e. identify themselves as bots), and to ban weak default passwords. Other states and countries…
























































































How Business Emails Are Vulnerable
Research by digital risk management and threat intelligence firm Digital Shadows has revealed that company credentials and emails that can be easily accessed on the web are making it easier for cyber-criminals to target businesses with attacks.
What’s…
























































































Facebook Hack Keeps Getting Worse
As if the recent Facebook hack of 50 million user accounts that was discovered on 25th September wasn’t bad enough, it became apparent that it could also affect "Facebook Login" service, which allows other apps to use people's Facebook account…
























IT SECURITY UPDATES ISSUE 7
Hi again Jon and welcome to our latest ‘Essential IT Security Updates’ newsletter : essential reading for IT security and data protection leaders like you wanting to stay ahead of developments and news in this ever-changing sector. Feel…
























IT Security Updates Issue 6
The latest news from the sector sees the British Airways become the latest hacking data breach victim, the CBI held its annual Cyber Security conference which was headlined by the head of the National Cyber Security Centre among other sector…
























































































BA Security Fallout
A discovery of the file containing the code used in the recent hack of the British Airways website and app that affected 380,000 transactions has revealed that it only took 22 lines of JavaScript to cause the massive data breach.
Skimming
The…
























IT Security Updates Issue 5
Western Australia’s Government has found the perfect password management approach, that Air Canada’s hack could impact customers by increasing the risk of ID fraud, Deloitte publish cloud strategies to improve cyber security processes and…
























































































Superdrug Customers Informed of Hack
Superdrug is reported to have advised online customers to change their passwords after it was targeted by hackers who claim to have stolen the details of approximately 20,000 Superdrug customers.
Hundreds Compromised - Could Be More
To date,…
























































































New Australian Law Gets The Thumbs-Down From Tech Firms
In Australia, a new draft bill proposing ways for tech firms, software developers and others to assist security agencies and police has been given the thumbs-down by a major industry group over its ambiguity, and the potential security risks…
























IT Security Updates Issue 4
The ICO are investigating a 10 million user data breach at Dixons Carphone, the ICO have also hired a new director as a nod to a changing security landscape, Butlins have announced a major phishing attack resulting in 35,000 customer records…
























































































IBM Makes Test Version of New Stealth AI Malware ‘DeepLocker’
IBM has announced that it has created its own stealth, ultra-evasive AI malware called ‘DeepLocker’ that can evade all traditional cyber-security protection, hide in normal applications, and only strike when it is sure it has reached its…
























IT Security Updates Issue 3
The ICO has fined the UK Government’s historic sexual abuse inquiry after a “very distressing” data breach, CISCO promotes a new way of tackling cryptomining hacks, UK Government to launch consultation on changing the UK cyber security…
























































































10 Million Affected by Dixons Carphone Data Breach
Dixons Carphone has announced that, after a review following a hack of its customers’ data, 10 million customers rather than the original estimate of 1.2 million have actually been affected.
What Happened?
Back in June, Dixons Carphone announced…
























































































Departing CEOs Steal Intellectual Property Says Report
A new report by Code42 that surveying 1,634 senior company employees in the UK, US and Germany, has found that most CEOs take what they regard to be their Intellectual property (IP) with them when they leave a company.
It Belongs To Me
The…
























IT Security Updates Issue 2
Major tech giants aren’t “respecting” the GDPR, the ICO is offering grant funding for ‘innovative’ research into data privacy, Ticketmaster subject to ICO investigation after major breach and more…
BEUC argues tech giants’ privacy…
























































































£500,000 Fine For Facebook Data Breaches
Sixteen months after the Information Commissioners Office (ICO) began its investigation into the Facebook’s sharing the personal details of users with political consulting firm Cambridge Analytica, the ICO has announced that Facebook will…
























































































NHS Booking App and Doc Bot
In the NHS's 70th year, and as part of the push for digitisation, the introduction of an appointment-booking app has been praised, while a GP chatbot has been given the thumbs-down by The Royal College of General Practitioners (RCGP).
Book…
























IT Security Updates Issue 1
The ICO have fined BT for a 5 million customer email ‘spam’ campaign that was found not to have ‘customers’ consent’, the ICO have also fined Gloucestershire Police an eye-watering £80,000 after an horrendous email error resulted…
























































































834% Rise in TSB Customer Attacks
Following the IT ‘meltdown’ at TSB last month which led to chaos for customers who were locked out of their own accounts, research has found that the number of phishing attacks targeting TSB customers leapt by 843% in May compared with April.
Fraudsters…
























































































Data Breach Fine For UK University
The Information Commissioner (ICO) has imposed a fine of £120,000 on the University of Greenwich for a data breach that left the personal details of thousands of students exposed online.
What Happened?
The breach was discovered back in February…
























































































TalkTalk Super Router Security Fears Persist
An advisory notice from software and VR Company IndigoFuzz has highlighted the continued potential security risk posed by a vulnerability in the WPS feature in TalkTalk's Super Router.
What Vulnerability?
According to IndigoFuzz, the WPS connection…
























































































Google Chrome’s ‘Incognito’ Mode Not So Incognito
Research by Internet Privacy Company DuckDuckGo is reported to have produced evidence that could show that even in Incognito mode, users of Google Chrome can still be tracked, and searches are still personalised accordingly.
Incognito Mode
Going…


How to improve your Cyber Security
Cyber security has never been more important to businesses today, especially with the new GDPR (General Data Protection Regulation) coming into force in May 2018. Companies across the UK are facing more cyber-attacks than ever before…


Cloud Vs On-Premise
To cloud or not to cloud? It's a question a lot of clients are asking more often and is undoubtedly one of the biggest trends in the IT industry right now. The choice is usually based on a number of criteria's, making it a seemingly overwhelming…


How to AVOID scam emails
Scam emails, also known as phishing emails/attacks, are becoming increasingly more common as fraudsters come up with new tricks to try and steal your personal information and bank details. In some cases, the emails carry malicious software…


Cyber scams to watch out for this Christmas
The festive season is fast approaching and that means a lot of us are completing our Christmas shopping online. Typically through the websites of retailers due to attractive online deals and discounts. However, the season is also a very vulnerable…


How to recognise scam emails
Scam emails can be very convincing and fraudsters have increasingly been trying to make them look more believable. They leave you vulnerable to identity theft, information theft, abuse of your computer and even financial loss. There are many…

