The current high-profile attack on the National Health Service, French car factories and which is spreading worldwide has brought ransomware to the fore. What is it? What can you do about the current outbreak? How do you protect yourself going forward?
What is ransomware?
Grouped within what in technology circles is called malware, ransomware is designed to extract money for regaining access your data. There are four ways then can enter your IT systems –
- Links – Found in Social Network posts or sent via emails, clicking the link causes the ransomware to install onto your computer.
- Attachments – Emails arrive with software attached. Often this is designed to look like documents (e.g. PDFs or Word documents). Once opened, the ransomware is installed.
- Via websites – This can be referred to as a “drive-by-download”. Simply visiting a compromised website can cause an installation of the ransomware.
- Via Botnets – Using this other form of malware, you are infected via other computers already infected. These botnets are controlled via criminals who are paid to spread the infection.
When the ransomware enters your system, it will either lock your computers, begin by encrypting all your data so that you cannot access it – sometimes it will do both. Once this process is complete, it takes over your computer and demands money to unlock the data and allow you access.
What about the current outbreak?
If you are running Windows 7 (updated to Service Pack 1) and Windows 10 then you should already be updated, as long as you have installed all the updates currently available on Windows Update. Microsoft released a patch through a Security Bulletin MS17-010. You can manually install the updates from the previous link if you want to be sure. To be certain run Windows Update now, by clicking on the Start Menu and typing in Windows Update. When the item appears in your Start Menu, click on it and follow the on-screen instructions.
For Windows Server, follow the standard procedure for those machines. You can use Windows Server Update Services to ensure that any machines on your network have all the patches installed.
For other operating systems that are no longer receiving updates from Microsoft, a series of updates have been provided on a one-off basis You can access them with the following links:
- Windows Server 2003 Service Pack 2 x64
- Windows Server 2003 Service Pack 2 x86
- Windows XP Service Pack 2 x64
- Windows XP Service Pack 3 x86
- Windows XP Embedded Service Park 3 x86
- Windows 8 x86
- Windows 8 x64
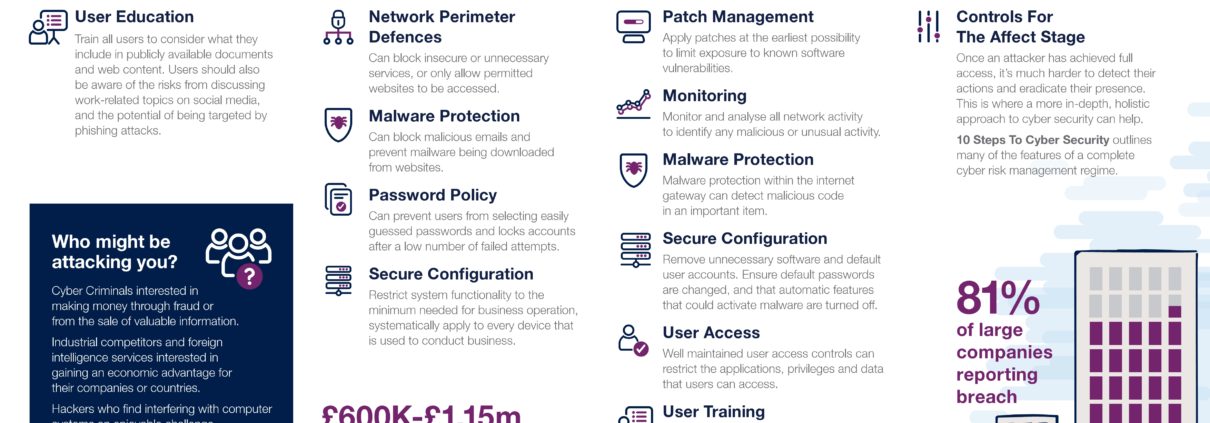
How do you protect yourself in general?
Good standard security practice always applies:
- Keep all your machines fully patched and up-to-date.
- If you are using Windows XP, Windows Vista, Windows 8 on your PCs and/or older versions of Windows Server, it is time to update to the latest version now. Other versions of Windows will lose support in due course, so start planning to move to current versions. See details of Microsoft’s maintenance policy.
- Make sure you have proper anti-malware software installed.
- Have a high-quality firewall installed and monitored.
- Follow standard practice – restrict Social Network access, do not click links in emails you were not expecting or open attachments
Consider having experts undertaking a full security audit of your systems and if you do not already have maintenance contracts in place, now is the time to think about it.
More general information can be found at the Government’s National Cyber Security Centre, who produced the info graphic above, which is used under the Open Government Licence.